What learning paths is this class used in?
Debugging, Reverse Engineering, Exploits
This is it! This is the class that *actually* teaches you how to exploit a race condition vulnerability leading to a use-after-free in the Kernel Transaction Manager (KTM) component of the Windows kernel. This class is meant to show the approach an exploit developer should take in attacking a previously unknown component in the Windows kernel.
The class is primarily focused around labs to teach the students what it takes to exploit a real-world vulnerability.
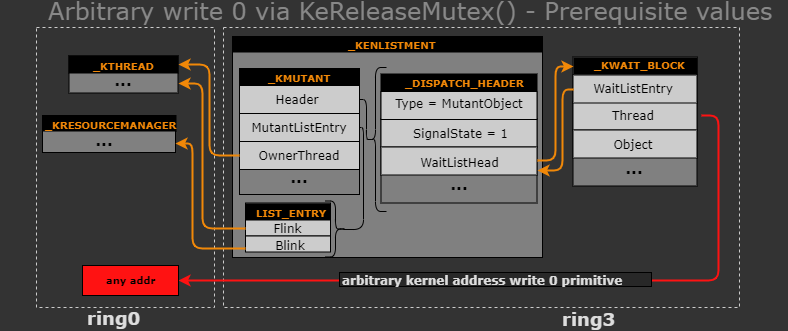
This class focuses on exploiting CVE-2018-8611 on Windows 10 x64 1809 (RS5), a complex race condition that leads to a use-after-free on the non-paged kernel pool. The vulnerability is in the Kernel Transaction Manager (KTM) driver (`tm.sys`), a component that has not yet received much public scrutiny.
Even though students will learn a lot about the KTM component, we focus on our approach for analyzing this component as a new kernel component that we had no prior knowledge about. The methodology can be reused for any other unknown kernel components a student may encounter in the future. We do not specifically focus on tricks or techniques for bypassing specific Windows versions mitigations, but rather on the thought process behind exploring functionality to find useful unmitigated code paths and also abusing the bug in ways that allow to build powerful primitives that would facilitate mitigation bypasses.
After this class, you'll know what it takes to develop an exploit targeting the Windows kernel.You must have taken OST2 Debuggers 3011 since we use the environment as a base for debugging/exploitation.
You must have taken OST2 Architecture 2821, or have equivalent knowledge of Windows internals.
Debugging, Reverse Engineering, Exploits
That is the question...

Cedric (@saidelike and @saidelike) is a security researcher specialised in vulnerability research and exploit development with over 15+ years of experience. He has been targeting lots of different components: mobile phones, Windows, Linux, firewalls, printers, routers, NAS with a focus on reliability and usability. He has won Pwn2Own in 2021 and 2022. He has been speaking at many security conferences (OffensiveCon, Hexacon, RECon, HITB). He is the founder of EZSecLab and is the maintainer of the "Windows Exploit Engineering Foundation" training.