What learning paths is this class used in?
Operating System, Architecture, Malware Analysis, Exploits
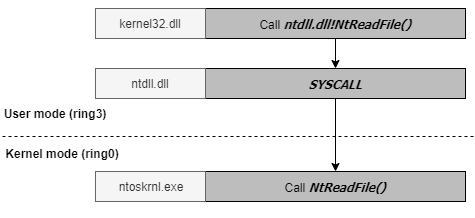
This is it! This is the class that *actually* teaches you some core concepts on the Windows operating system both in user and kernel lands. You'll learn about core kernel functionality, what you will typically encounter while exploiting kernels, and how to approach targeting any kernel, though all the internals explained apply to Windows only.
After this class, you'll have knowledge to analyze the Windows kernel.You must have taken OST2 Debuggers 1011: Introductory WinDbg and Debuggers 2011: Intermediate WinDbg, or have equivalent knowledge of WinDbg.
You must have taken OST2 Debuggers 3011, or have equivalent WinDbg environment configured.
Operating System, Architecture, Malware Analysis, Exploits
That is the question...

Cedric (@saidelike and @saidelike) is a security researcher specialised in vulnerability research and exploit development with over 15+ years of experience. He has been targeting lots of different components: mobile phones, Windows, Linux, firewalls, printers, routers, NAS with a focus on reliability and usability. He has won Pwn2Own in 2021 and 2022. He has been speaking at many security conferences (OffensiveCon, Hexacon, RECon, HITB). He is the founder of EZSecLab and is the maintainer of the "Windows Exploit Engineering Foundation" training.