What learning paths is this class used in?
Exploits, Reverse Engineering, Malware Analysis, and System Security
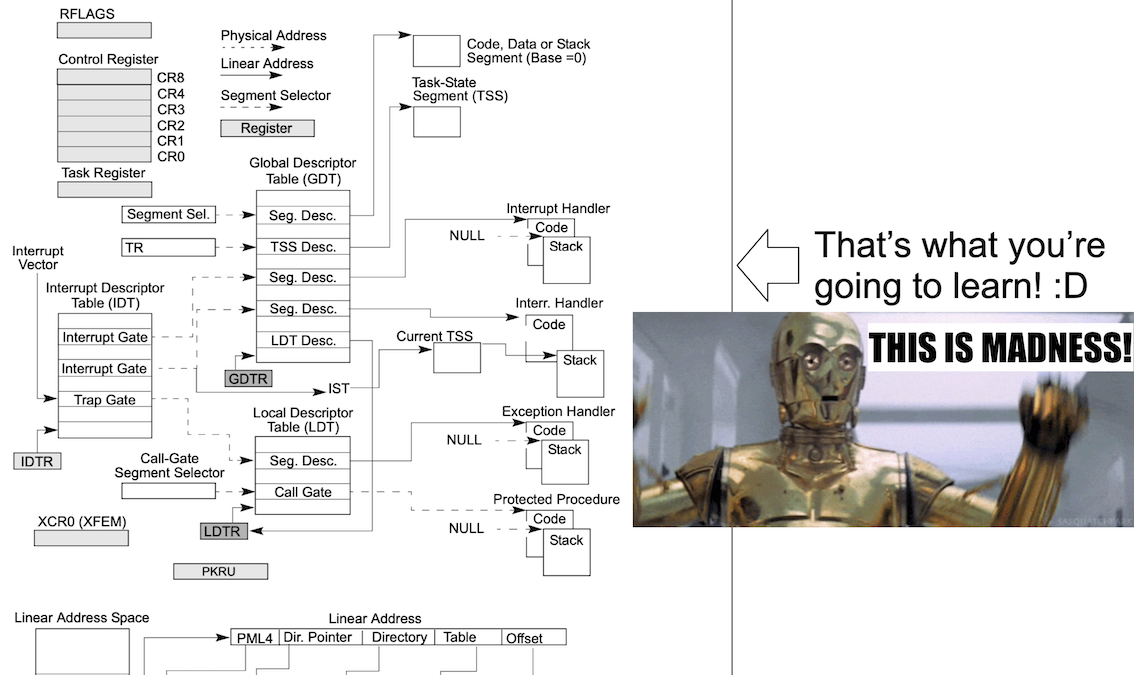
This is it! This is the class that *actually* teaches you how ring 0 vs. ring 3 privilege separation works at a deep deep level on Intel hardware!!! But so much more too! This class gives you an incredibly strong foundation for Windows, Linux, *BSD, or macOS OS Internals classes. Because if covers the hardware-specific requirements that every OS (or VMM or BIOS) must deal with if they want to run on Intel hardware.
After this class you will feel exploring wherever you want in the Intel manuals, because this class covers some of the most difficult to understand underlying technologies that OSes depend on.You must be comfortable with C programming.
You must have taken OST2 Architecture 1001, or have equivalent knowledge of assembly.
Exploits, Reverse Engineering, Malware Analysis, and System Security
Yes, but only occasionally. Upcoming trainings will be listed here, and private trainings can also be requested.

Xeno founded OpenSecurityTraining(1) in 2011 to share his and others' trainings more widely. He relaunched OpenSecurityTraining2 in 2021.
Xeno's from Minnesota and has a BS in CS from UMN. He received a MS in computer security from Carnegie Mellon through the National Science Foundation "CyberCorps Scholarship for Service". But the US government didn't really yet know what to do with "cyber" people in 2007; so he ended up going to work for a Federally Funded Research and Development Center - MITRE. Xeno worked exclusively on internal-funded research projects, first as a participant and later as a leader on Windows kernel malware detection and trusted computing projects. Towards the end, other cool researchers inspired him to dig into BIOS and firmware level threats.
Xeno left MITRE to start an independent consultancy, LegbaCore, with Corey Kallenberg in 2015. Less than a year later, under mysterious circumstances that he's legally prevented from stating, he started working for Apple. While at Apple he helped get SecureBoot on Macs with the addition of the T2 chip. He also led the SecureBoot design and implementation project for the ARM-based M1 Macs. But between those big, visible, multi-year, projects, he was silently improving the security of a bunch of the 3rd party peripheral processors' hardware and firmware. He liked working at Apple because he had a bully pulpit where he could force 3rd parties to do the right thing or lose their business. But he likes OST better, so he left in 2020 to work on this full time.
Xeno has a touch of the illness known as being a "collector" (it's not quite to the level of being a "hoarder", so he can't get on TV for it or anything...) Consequently he collects speaker badges and has presented at IEEE S&P, ACM CCS, BlackHat USA/EUR, Defcon, CanSecWest, PacSec, Hardwear.io NL, Hack in the Box KUL/AMS/GSEC, H2HC, Microsoft BlueHat, Shmoocon, Hack.lu, NoHat, Hacktivity, HackFest, NoSuchCon, SummerCon, RSA, ToorCon, DeepSec, VirusBulletin, MIRCon, AusCERT, Trusted Infrastructure Workshop, NIST NICE Workshop, and the DOD Information Assurance Symposium. And yet he still says "MORE!"